Global cybersecurity agencies have announced a list of the top 15 vulnerabilities exploited by threat actors throughout 2021.
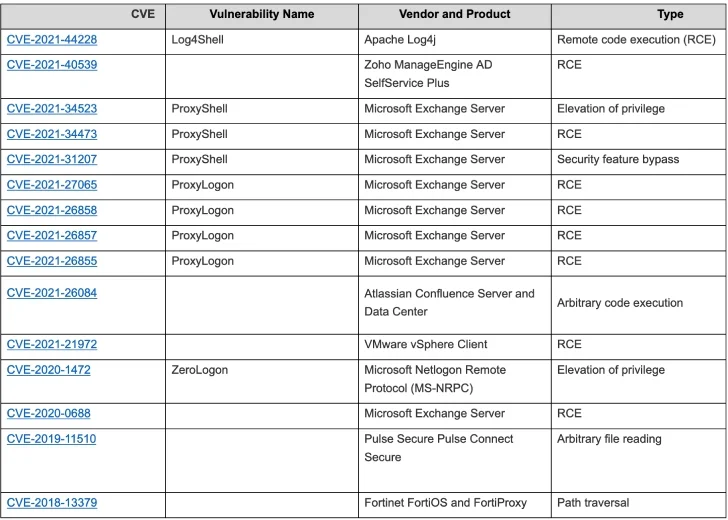
Among those that topped the list were Microsoft and Atlassian bugs, and the Log4Shell vulnerability – the latter of which is still in circulation today. Microsoft accounts for 9 out of the 15 top exploits listed in the report.
The agencies, that were in partnership with the Federal Bureau of Investigation (FBI), the National Security Agency (NSA), and the Cybersecurity and Infrastructure Security Agency (CISA), stress that organizations need to do more to identify and manage these malicious actors, some of which have been targeting virtual private network (VPN) servers and emails to deploy their malware.
Cybersecurity Agencies Revealed The 15 Top Routinely Exploited Vulnerabilities
After over 20,000 common online vulnerabilities were disclosed in 2021, a global suite of cybersecurity organizations – alongside the US’s most notable security agencies – have identified the most commonly occurring threats.
The Five Eyes intelligence partnership, comprised of authorities from the US, Australia, Canada, New Zealand, and the UK, found that the top bugs were Log4Shell, the Microsoft vulnerabilities ProxyShell, ProxiLogon, and a bug affecting Atlassian products.
We know these CVEs were frequently exploited in 2021, including some disclosed in 2020 or earlier. Mitigate and patch. These are the unlocked doors! https://t.co/LjMkdqaIVo
— Dave Luber (@NSA_CSDirector) April 27, 2022
According to an official release from CISA, three of the top 15 vulnerabilities were also being exploited in 2020. These include the Windows CVE-2020-1472 bug, which targets Microsoft servers, the CVE-2018-13379 bug, which was used to leak the credentials of over 87,000 Fortinet VPNs, and the CVE-2019-11510 bug, which was exploited by Russian actors to target US infrastructure sites.
“We know that malicious cyber actors go back to what works, which means they target these same critical software vulnerabilities and will continue to do so until companies and organizations address them” explains CISA Director Jen Easterly.
“CISA and our partners are releasing this advisory to highlight the risk that the most commonly exploited vulnerabilities pose to both public and private sector networks,” – Jen Easterly, CISA Director
The report also warned that exploited proof-of-concept codes were partly responsible for the growing number of attacks. The codes, which are developed by IT researchers to demonstrate security flaws, are commonly released weeks after the vulnerabilities disclosure.
Once released, these codes often fall into the hands of malicious actors, where they can be used to target and extort an even wider network of organizations. And these stunts aren’t happening on a small scale. The mass exploitation of a proof-of-concept code was behind the Atlassian bug, which was one of the most widespread vulnerabilities cited on the list.
When asked if proof-of-concept codes should be kept private, CISA explained that these codes provide “a net benefit to network defenders, allowing them to validate patches and test mitigations.” This suggests that the threat of proof-of-concept vulnerabilities isn’t set to fade anytime soon.
The Malicious Log4Shell Bug Is Still At Large
CISA’s report also revealed that some bugs – like Log4Shell – are still being exploited to this day.
Despite a global campaign to patch the vulnerability, the cybersecurity authorities have found that it is still being used by dangerous actors.
“The breadth of the issue and the difficulty in determining what was affected means that this will have a long tail to it” – David Wolpoff, CTO of Randori
For instance, the bug, that was discovered in December, was recently utilized by the North Korean government to hack into an unnamed engineering company with military customers.
Yotam Perkal, vulnerability researcher at cybersecurity firm Rezilion, also adds that 68,000 public-facing internet servers and 90,000 machines are still vulnerable to the Log4Shell bug, with David Wolpoff, CTO of security company Randori adding that the vulnerability was one of the worst he’s seen in his career.
What Advice Do These Agencies Have For Businesses?
Knowing about these risks is all well and good. But what practical advice have the security authorities given to businesses?
Well, according to this recently released report, the agencies recommend the following mitigations:
- Update software, operating systems, and applications regularly
- Use a centralized patch management system to patch vulnerabilities as soon as they become known
- Enforce multi-factor authentication across all areas of your business – especially on VPN connections
- Use private local area networks when possible
- Limit the use of third-party applications
- Disable unused network ports, protocols, services, and devices
- Use security tools such as endpoint management software




