Our content is funded in part by commercial partnerships, at no extra cost to you and without impact to our editorial impartiality. Click to Learn More
Take a look at the latest ransomware statistics and it’s easy to see why it is regarded as one of the biggest cybersecurity threats around.
Ransomware targets businesses of all shapes and sizes, but a common thread is this: easy targets are most likely to fall victim to an attack. Make sure your organization isn’t one of those underestimating the threat.
In our in-depth ransomware guide, we’ll cover everything there is to know about the current landscape, highlighting the latest ransomware trends alongside our own expert insights. If knowledge is power, then this article features all the information you need to both understand ransomware and defend your business against it.
Key Stats to Know
- Ransomware is a growing threat to businesses of all sizes. In 2022, 73% of businesses suffered a ransomware attack, and the global cost of ransomware is expected to exceed $30 billion in 2023.
- The average ransomware attacker demanded $1.5 million in 2023. However, over 80% of people who pay a ransom will be attacked again.
- Ransomware attacks often start with a simple email. In 69% of cases, the ransomware payload is delivered via email.
- Ransomware attacks can have a devastating impact on businesses. In 40% of cases, companies that suffer a ransomware attack will lay off employees as a result.
- There are steps that businesses can take to protect themselves from ransomware attacks. These include using strong passwords, backing up data regularly, and using security software.
- Investing in security will save you money. Organizations that employ AI security and automation systems can save an average of $3 million in data breach costs.
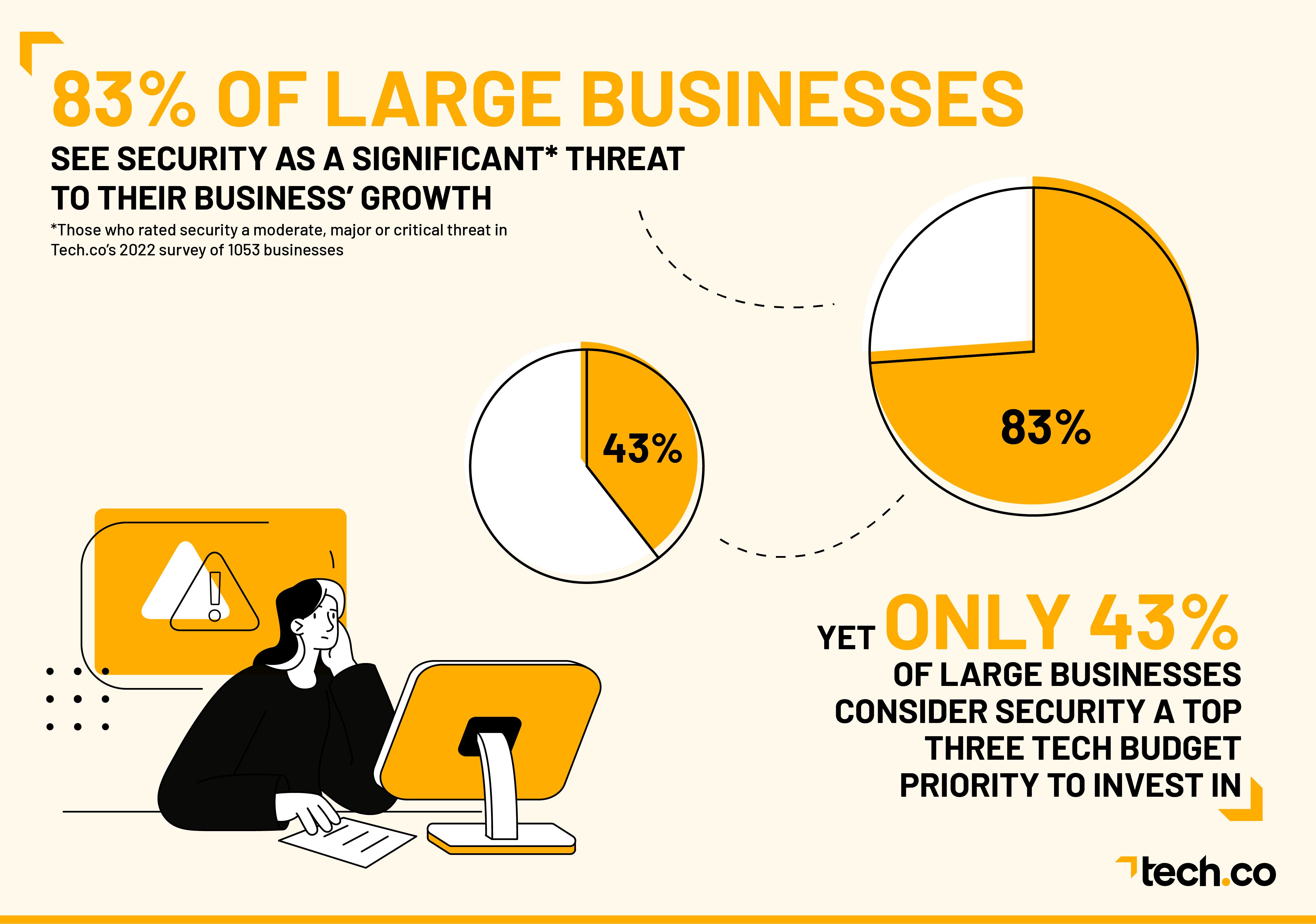
- Despite the growing threat of ransomware, many businesses are not adequately prepared. Only 43% of large businesses consider ransomware a top 3 investment priority.
All these statistics and more are explained in full, along with their sources, below.
On this page, we’ll answer all the most common questions about ransomware, starting with what it is and how it works. Small businesses in particular will want to read on as a matter of importance, as many won’t be able to sustain the damage – both reputation and financial – that comes with suffering a ransomware attack.
Having been immersed in the world of business technology for nearly two decades, you can trust us to help you get to grips with the latest cybersecurity threats and bring you all the most relevant ransomware statistics in one handy place.
What Is Ransomware? Is Ransomware Malware?
Ransomware is a specific type of malware that holds files or even entire devices hostage, and demands a payment to release them. It’s one of the most common forms of cyber crime and started to emerge threat around 2013.

Currently, ransomware is thought to be responsible for nearly a quarter (24%) of all global attacks, according to Verizon’s 2023 DBIR report, and it’s one you may well be familiar with, since 73% of organizations reported falling victim to a ransomware attack in 2022, according to Barracuda’s research.
- 82% of ransomware attacks target small businesses.
- The US is the most attacked country, fielding 25% of all ransomware attacks.
- Critical US infrastructure was hit 860 times by ransomware in 2022. Healthcare is the most targeted industry.
How Does Ransomware Work?
Ransomware attacks see cyber criminals take over a victim’s device and then use encryption to block access to the machine, specific files and data, or both. They then hold it to ransom, with the amount of money demanded varying wildly.
Sophos puts the global average payment at $1.5 million for 2023, though the overall cost to organizations is much higher, with IBM’s 2022 Cost of Data Breach report saying it costs companies an average of around $4.5 million. This is why the global cost of ransomware attacks is so astronomical.
- Global ransomware damages were estimated to exceed $30 billion by 2023.
- Despite this, less than half of large US Businesses are investing in cybersecurity.
Geography plays a huge part in how much threat actors will demand, with further Sophos data revealing that UK firms are leveraged for an average of £2.1 million – way above the global average.
When a ransom is paid, usually by Bitcoin or another cryptocurrency, the cyber crooks promise to send the victim a decryption key or relinquish control of the affected website. Companies or individuals that refuse to pay are threatened that their data will be leaked in public, sold on the dark web, or permanently deleted.

That’s the big question, and the answer is a resounding no. Security experts are unanimous in saying that you should never pay a ransomware demand, with the statistics backing this up.
- CyberReason’s 2022 Ransomware report highlights that 80% of businesses that pay a ransom will be attacked again.
- Sophos’ study reveals that a mere 4% of organizations that pay up recover all of their data.
You don’t have to be a genius to work out that this is a false economy. Organizations still do pay up, of course, and we’re not saying that’s wrong, to retrieve what is considered precious property.
But the data would strongly suggest the short-term convenience of getting (most of) your data back is voided by the fact you’ve placed a dollar sign target on your back, which is likely to attract future criminals.
Why Do Ransomware Attacks Happen?
The cause of ransomware attacks can vary greatly, but financial gain is the usual motive for cyber criminals. In some cases, they may be politically or ideologically motivated.
The cause of ransomware attacks is also subject to debate, though the fact that as much as 50% of US small-to-medium size businesses admit to not having a cyber security plan in place suggests a common theme is the vulnerability.
In some cases, the victim isn’t even selected by the ransomware gang responsible for creating the virus – they’re picked by a third-party, who buys the ransomware from the cyber criminals along with instructions in what’s now being called RaaS, or ransomware-as-a-service.
Wait, what is Ransomware as a Service?
A devious variation on the traditional Software-as-a-Service (SaaS) business model and the latest abbreviation sweeping the world of online security. RaaS, or ransomware as a service, is when cyber crime groups sell their ransomware to third-party affiliates, who then deploy it against targets themselves.
Typically, the affiliates will lack the ability to develop their own ransomware, so they simply purchase a pre-packed RaaS ‘kit’ on the dark web that may include things like 24/7 support and bulk discounts. Security outfit Crowdstrike reports that these can be bought for as little as $40 a month.

Look away now, IT and compliance pros: by far the most common root cause of ransomware attacks is email phishing campaigns. According to security researchers at Barracuda Networks, 69% of ransomware attacks are borne out of email phishing, which isn’t a new trend but appears to have been amplified recently, as phishing emails are now even being written by AI.
Once user credentials are compromised, threat actors are then able to complete a system takeover or get their hands on the sensitive data they then encrypt.
The laxer security practices associated with working from home have accelerated attacks even further. Ransomware statistics show a 300% spike in 2020, which is the period when Covid-19 forced organizations to shift exclusively to home working – many for the first time and without a blueprint for what WFH security best practices looked like.
Further evidence is the continued surge in ransomware from 2020 to 2021, when attacks more than doubled from 304m to 623m at the height of remote working, followed by a dramatic dip to 493m incidents in 2022, by which time companies had both put into place robust remote working measures and started to return to the office.
The number of companies offering remote working arrangements was still sizable in 2023, as is the ransomware threat, but a return to pre-pandemic normality (rather than the infamous ‘new normal’) appears to be leveling the playing field.
What are the Consequences of Ransomware Attacks?
The fallout from ransomware attacks can be catastrophic, especially for small businesses operating on razor-thin margins. This is because ransomware is a lose-lose situation whatever the size of your organization. If you pay the demand, you’re out of pocket and likely to be targeted by future attacks. If you don’t, your data is likely to be leaked and this has financial consequences of its own.
Either way, the reputational damage can’t be underestimated and the business you’re likely to lose as a result can have far-reaching implications. Ransomware statistics reveal 40% of companies that suffer a ransomware attack lay off employees as a result, with 35% witnessing C-level resignations. Sure, some of the rolling heads are likely to be down to boardroom blame games, but it’s still worth remembering that the damage of a ransomware attack doesn’t go away the moment you regain access to your data or devices.
- 46% of organizations reported a significant loss of revenue following a ransomware attack in 2022.
- 63% of victims found their attackers had remained undetected for 6 months or more.
- 40% of companies that suffer a ransomware attack layoff employees as a result
- 45% of cybersecurity professionals have considered quitting over the constant threat of ransomware attacks
- Organizations that employed AI security and automation systems saved an average of $3 million in data breach costs
What are some examples of ransomware attacks?
Three examples of ransomware that illustrate the devastating effect it can have are the WannaCry, NotPetya and Colonial Pipeline attacks.
WannaCry
By all accounts, 2017’s WannaCry ransomware attack is the benchmark for these kinds of incidents and one of the most alarming cybersecurity case studies in history due to the kinds of institutions affected and how quickly it spread. In just eight hours — before a ‘kill switch’ for the attack was discovered — more than 300,000 computers were infected across 150 countries. The attack affected big name companies like Nissan, and critical infrastructure like the National Health Service (NHS) in the UK. It was eventually attributed to North Korea.
NotPetya
Also staged in 2017 and notable for being a regular malware attack disguised as ransomware is the NotPetya attack. This means its sole purpose was to cause chaos and the demands for payment it featured were actually a false flag, or distraction, from its true nature: a simple ‘wiper’ virus designed to inflict maximum damage. NotPetya primarily targeted organizations in Ukraine, including its financial, energy and government institutions. Various global cybersecurity agencies hold Russia responsible
Colonial Pipeline
Arguably the most impactful ransomware attack in US history, Colonial Pipeline saw the oil pipeline system of the same name targeted by the Russia-based DarkSide ransomware group. It shut down pipeline operations for six days, resulting in a state of emergency being declared by both the Federal Motor Carrier Safety Administration (FMCSA) and President Joe Biden, due to resulting gas shortages. Somewhat surprisingly, the FBI oversaw payment of the ransom to the tune of 75 Bitcoin, or more than $4.4 million at the time. The Department of Justice recovered a little more than half of that, though no one has ever been brought to justice over the attack.

When it comes to preventing ransomware attacks at your business, you’ll hear a lot about “having a robust cybersecurity plan” in place. This kind of vague advice isn’t particularly helpful, in our opinion. Here are some practical things you do as part of developing your overall cybersecurity strategy, as well as why they will actually help.
Read our guide to small business cybersecurity measures to protect your business
1) Regular software updates
Many of the most crippling ransomware attacks exploit system vulnerabilities. WannaCry is one such example and was staged via a backdoor, or flaw, in Microsoft’s Windows operating system. Keeping your systems and software up-to-date is therefore essential, as these updates contain patches for flaws just like the one used by the WannaCry cyber criminals to such devastating effect.
This golden rule applies to all the software your business might be running, right down to the web browsers used by employees. We all know the relentless stream of update notifications on computers are a pain these days, but they may just save your bacon.
2) Employee training and education
It’s all well and good saying you need to update your systems regularly, but what if your employee keeps hitting the snooze button? Make the process easier by ensuring your workforce is adequately educated as to why security best practice is so important.
With email phishing so prevalent as a means of attain the credentials used to instigate ransomware attacks, one specific way you can fight back is by your IT department staging test phishing campaigns to gauge your employee’s level of readiness. Those who report the messages as suspicious are likely prepared, while those who don’t may need to revisit security best practice.
Given time is money, it may seem like setting aside the hours for comprehensive security training is an expensive task, but it’s far more cost-effective than coughing up a ransomware demand. Still not convinced? According to Verizon’s 2023 DBIR report, a whopping 74% of all data breaches are down to human error in one form or another.
3) Data backup and recovery systems
Safeguarding yourself against ransomware attacks isn’t just about prevention – you also need to account for what happens in a worst case scenario. Peace of mind is on offer if you’ve got your data adequately backed up and able to be recovered, should your systems be compromised.
Data backup and recovery solutions are somewhat self-explanatory. Here’s how they work: all your data gets duplicated and stored in a secure location. In the case of data loss, damage, or ransoming, you can restore it to a new system that hasn’t been breached. This means your operational downtime and the financial damage that comes with it will be minimized, as you’ll be able to use your data again as soon as it’s restored.
4) Equip yourself with the right tools
Keep cyber criminals at bay by using the right software at your organization. Specifically, you’ll want to seriously consider VPNs, password managers, and of course antivirus solutions. Let’s take a closer look at what some of these are and why you should use them.
Why Your Business Should Use a VPN
VPNs, or Virtual Private Networks, are clever bits of software that reroute internet activity via anonymised servers all over the world, effectively masking your IP address and encrypting any data that passes over the connection. With sharing documents over Dropbox and Google Drive now commonplace at small businesses, adding this extra layer of security comes highly recommended as these documents may include the shared credentials so often used to launch ransomware attacks.
When it comes to selecting a VPN, you’re spoilt for choice. After extensive research, we can confidently say that NordVPN is the most secure VPN around. It’s affordable, with pricing starting from just $3.29 a month, and even offers a 30-day money back guarantee. Depending on the size of your small business, you can also look at its enterprise-ready NordLayer product.
However, there are plenty of other VPNs should Nord not be the right fit for your needs. Surfshark offers a great deal for global users, for example. View more top VPN picks in our table, below.
| Test Score Our scoring is based on independent tests and assessments of features, privacy settings, ease of use and value. | Price From Lowest price for single month subscription to cheapest paid tier. Other plans are available. | Verdict | Free Trial | Try Click to find the latest offers, deals and discounts from the VPN provider | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| BEST ON TEST | ||||||||||
| 4.0 | 4.3 | 3.8 | 3.7 | 4.0 | 4.1 | 3.8 | 4.3 | 3.9 | 4.3 | 3.5 |
| $3.39/user/month (Up to 72% off!) | $2.99/month | $2.03/month | $9.99/month | $3.00/month min. ($1 per location) | ~$4.87 per month | $2.19/month | $4.99/month (with two-year commitment) | ~$2.20 (3-day plan) | ||
| Super fast and easy to use, NordVPN is among the best we’ve tested. Advanced features like Onion-Over-VPN make it stand out from the crowd. | An excellent price for a powerful VPN tool with an adblocker, malware detector and no limit on the number of devices you can use it on. | A fast VPN that performed well on our speed tests, and also owns a lot of its own server infrastructure. | Affordably priced ultra-secure VPN that has great privacy features but is a little slow. | A reliable, widely-used VPN that has decent privacy controls, but it performed very poorly on our speed tests. | A safe, easy-to-use and relatively robust VPN app that performed really well on our 2024 unblocking tests. | A decently-priced VPN that does all the basics well, but has an incredibly small server network compared to PureVPN and Co. | A decent option for seasoned torrenters, but a little pricier than PureVPN and Private Internet Access. | A user-friendly VPN based in Romania with servers optimized for streaming, but no obfuscation technology. | A highly reliable VPN with servers in more than 100 countries – but it comes with one of the heftiest price tags on the market. | A powerful tool for expert users |
| 30-day money-back guarantee | | Yes (iOS and Android) | | | 7 days | | | | 30-day money-back guarantee | |
| See Deals | See Deals | See Deals | See Deals | See Deals | See Deals | See Deals | See Deals | See Deals | See Deals | See Deals |
Why Your Business Should Use a Password Manager
Recycling is a good thing. Recycling the same password across multiple accounts and devices? That’s not so hot. Yet many otherwise diligent employees do just that, faced with trying to remember a slew of complex combinations. The consequences can be catastrophic, as we’ve learned from the shocking number of ransomware attacks that are enabled by stolen or misused passwords.
It follows that making it easy for employees to manage their passwords is a simple yet highly effective way of upping your online security. Having the right tools is the key and our in-depth research selects NordPass as the top overall password manager. It comes competitively priced from just $2.99 a month, though the Family Plan nets you six users for $5.99 a month and is the best overall value.
For larger organizations, NordPass has a dedicated Business Plan priced at $3.59 per user, per month. That’s our pick of the bunch, but to see what else is out there check out our full guide to the best password managers, or the table below.
| Local Storage Option | Two-Factor Authentication | Failsafe Function | Password Generator Function A password manager can create secure, complex passwords for you. You won't need to remember them yourself. | Help Instructions | Email Support | Live Chat Support | Phone Support | Price | Business Plan? | Business Price Cheapest available business plan | Click to Try | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FEATURED | TOP PICK | ||||||||||||
| NordPass | LastPass | Dashlane | Sticky Password | ||||||||||
| | | | | | |||||||||
| | | | | | |||||||||
| | | | | | |||||||||
| | | | | | |||||||||
| | | | | | |||||||||
| | | | | | |||||||||
| | | | | | |||||||||
| | | | | | |||||||||
| $1.69/month | $2.40/month | $8 per user/month | $19.99 per year | ||||||||||
| | | | | | |||||||||
| $19.95/10 users | $2.51 user/month | $3.20/user/month | $60/user | $29.99/user/year | |||||||||
| Try 1Password | Try NordPass | Try LastPass | Try Dashlane | Sticky Password |
Why Your Business Should Use Antivirus Software
If you haven’t already, make sure to check out the best antivirus software for business. Having good antivirus software means it’s no longer solely your responsibility to stay on top of the latest vulnerabilities and threats – you’re enlisting the help of the experts as well.
Antivirus software’s job is to detect and eliminate threats before they take hold of corporate devices. They’re especially good when it comes to ensuring systems remain fully patched and updated against the latest viruses and exploits, so they can’t be preyed on by bad actors and their malware.
Most antivirus solutions these days also come with ransomware-specific protection, with some even coming with ransomware removal tools. You’ll never be able to guarantee you won’t fall victim to an attack, but as criminals tend to select the easiest targets, you’re making the chances far less likely.
| Price Per year, unless stated otherwise | Pros | Cons | ||
|---|---|---|---|---|
| Best for Small Business | Best Value | |||
| BitDefender GravityZone Business Security | Surfshark One | Norton Small Business | Avast Business Security | McAfee Total Protection |
| $3.49/month (12 month subscription) |
|
|
|
|
|
|
|
|
|
|
|
|
|
Ransomware: A Summary
It’s clear that ransomware is one of the most dangerous IT security threats around in the modern era of the internet.
The damage caused by attacks can be crippling for organizations of all sizes, but especially for small businesses whose reputation and bottom line may not be able to withstand the fallout.
There are several measures you can take to protect your company against falling victim to cyber criminals in this way, but arguably the biggest step you can take is also simplest: realizing that the threat is real. Once you accept ransomware attacks can and very possibly will happen to your business, choosing the right tools and investing in a serious cybersecurity plan becomes a whole lot easier.
Learn more about security in the physical world with our guide to the latest shoplifting statistics.
If you click on, sign up to a service through, or make a purchase through the links on our site, or use our quotes tool to receive custom pricing for your business needs, we may earn a referral fee from the supplier(s) of the technology you’re interested in. This helps Tech.co to provide free information and reviews, and carries no additional cost to you. Most importantly, it doesn’t affect our editorial impartiality. Ratings and rankings on Tech.co cannot be bought. Our reviews are based on objective research analysis. Rare exceptions to this will be marked clearly as a ‘sponsored’ table column, or explained by a full advertising disclosure on the page, in place of this one. Click to return to top of page





















