Microsoft Authenticator has just introduced number matching to its app, in an attempt to crack down on its biggest Achilles heels — MFA fatigue attacks.
Number matching adds an extra layer of security to the login process by requiring users to input a digital code when verifying their accounts, and will now become the default for everyone using the app.
As an increasing number of US companies fall victim to MFA fatigue — including Cisco, Uber, and Microsoft themselves — this security upgrade marks a promising step in the right direction.
If you’re unfamiliar with number matching or MFA fatigue, we break down what this new feature could mean for you, and why it could be such a game-changer.
Microsoft Authenticator Is Now Enforcing Number Matching
If you’re a Microsoft Authenticator user, your experience with the app will be changing, as the authentication app has just added number matching to its security arsenal.
Starting on May 8th, the extra layer of verification has been enabled for all Authenticator push notifications. This means that when verifying their identity, users will now need to transfer a two-digit code from their secondary to their primary device, preventing them from authorizing a login attempt by mistake.
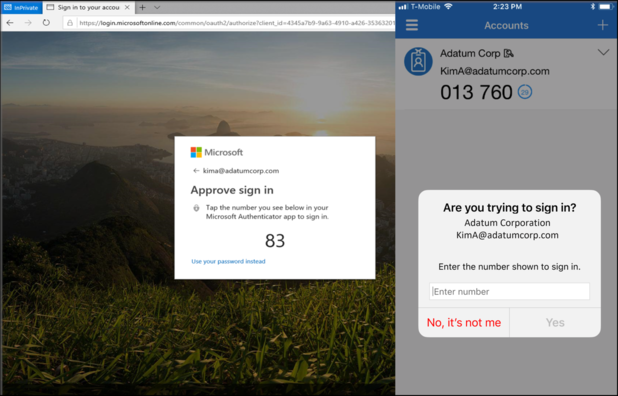
Number matching will now become customary for everyone who uses Microsoft Authenticator as their default verification method, and will also be available to users resetting their own password or registering for the app.
“If the user has a different default authentication method, there’s no change to their default sign-in. If the default method is Authenticator, they get number matching.” – Microsoft’s blog post
Microsoft isn’t the only company to bolster its security with number matching, though. In fact, the Cybersecurity and Infrastructure Security Agency (CISA) recommends that all organizations enable the safeguards to prevent MFA fatigue.
What exactly is MFA fatigue, and how has it become one of the top cyber concerns for businesses in 2023?
A Promising Stand Against MFA Fatigue
MFA fatigue is a relatively new social engineering strategy that’s been deployed by cybercriminals a lot in recent years.
Also known as “MFA spamming” and “MFA bombing,” the action exploits MFA solutions by overwhelming users with a string of requests for sign-in approval, with the ultimate aim of gaining access to the individual’s network.
While this technique may seem easy to dismiss, attempts can seem convincing, with hackers also sending out emails posing as IT support in many cases to make these requests seem more valid.
Due to the simplicity and high success rate of the attack, the practice has been growing more widespread year after year, with Microsoft attributing 382,000 attacks to MFA fatigue in 2022 alone.
It’s not just catching small fish, either, with the technique being involved with a series of attacks on large corporations with dedicated security teams like Uber, Microsoft, and Cisco.
Currently, number matching is one of the most effective ways to crack down on MFA fatigue, so Microsoft Authenticator users should welcome this change with arms. The measure helps MFA and 2FA — already two of the most secure authentication methods — become even more safe.
But not every network is using forms of multi-factor authentication. So, if your organization is still relying on passwords to protect its systems, you can brush up on our password security guidance here.





