Cybersecurity attacks are now a common fixture of the digital landscape, but not enough people take password security seriously. Testing your password strength is one of the most overlooked yet vital steps in protecting your online accounts. Password managers are also key to giving you a better chance against hackers.
Weak, easy-to-crack passwords are still used en masse, and a lot of people use the same password across multiple accounts they own, leaving all of their data dangerously exposed to those trying to steal it.
In this guide, we take a closer look at precisely how long it takes to crack a password, the most common methods used to do this, and how you can improve your password security.
- How Long Does It Take to Crack a Password?
- The Factors Affecting Password Cracking Time
- Password Cracking Methods
- Other Ways Hackers Can Obtain Your Password
- How to Improve Password Security
- Passwords vs Passphrases
- Final Thoughts: Securing Your Accounts Today
- Password Cracking: FAQs
How Long Does it Take to Crack a Password?
How long it takes to crack a password varies depending on the range of characters you use, as well as the length of the password in question.
Cybersecurity firm Hive Systems has produced some time estimates for password. As you can see, a 7-character password can be cracked in just two seconds, even when numbers, upper case letters, and lower case letters are utilized:

Hive calculated these time estimates by working out how long it would take to crack different types of passwords after acquiring their “hash” values.
“Hashing” is a concept in computing used to protect passwords, within which a collection of characters (i.e. a person’s password) is transformed into some other value.
When you input a password into a website, the website will only save your hash, rather than your password. This means social media sites, streaming services, and other businesses that offer user accounts can avoid keeping a dataset of every account holder’s password.
Expert Tip
A lot is noise is often made about ensuring sure your password is long and complex enough to withstand common password-cracking tactics, but uniqueness is just as important. Reusing a password across multiple sites that contain personal information means there’s only one key – and one door – behind which all of your sensitive data is hidden. Uniqueness is vital, as is finding a secure place to store your passwords.

The Factors Affecting Password Cracking
As you can see from the above table, there are two main factors that affect password cracking: length and complexity.
The shorter your password, the less time it’ll take to crack. And if you exclusively use one variety of characters, such as numbers, this makes your password significantly less secure – variety is also important.
Another factor that affects password hacking is whether the hacker targeting you has a tool that can automate password-cracking methods, such as brute-forcing (more on this later). Of course, this isn’t a factor within the user’s control, but it reinforces the importance of making your password strong and complex.
If you re-use a password on multiple sites, this will decrease the time it takes to crack your accounts on those sites down to0, if a hacker is able to obtain your password for just one.
Password Cracking Methods
Brute forcing
Brute-forcing is perhaps the most infamous form of password cracking. As the name suggests, it’s not particularly complex – it’s a trial-and-error method that is the cybercriminal’s equivalent of a medieval army’s battering ram. There are three main types:
Simple Brute Forcing: A hacker will pick a target, and then try lots of very basic, common passwords (e.g. Password123) in the hope the victim has used weak credentials.
Dictionary Attacks: While not considered a true brute-forcing technique, dictionary attacks still embody the trial-and-error spirit. In these attacks, hackers will try all the words in a dictionary (although often this is streamlined to common words/phrases), replacing letters with numbers. This is a relatively cumbersome way to brute-force an account.
Reverse Brute Forcing: In reverse brute-forcing attacks, instead of trying lots of passwords against one username, the attacker will try a single password against lots of usernames, typically leaked online during a data breach.
As mentioned previously, there are now tools available that can automate much of the brute-forcing process, so hackers can try thousands of passwords in minutes.
Credential stuffing
Once a hacker has guessed a target’s password for one site, they can crack passwords for other sites using a technique called ‘credential stuffing’.
In a nutshell, the hacker will try the username and password combination for one site on a string of other popular websites (such as Facebook or Twitter). This is why it’s so crucial you don’t repeat passwords across multiple accounts.
Rainbow table attacks
As we’ve mentioned previously, to avoid storing huge databases of plain text password credentials, “hash” keys are stored instead. This is a string of values that a password is converted into and can be used for future authentication.
When a user returns to the site, the password they enter is converted into a hash value and cross-referenced with the hash values stored in a given website’s database.
Rainbow tables are effectively an index of commonly used plain-text passwords with their corresponding hashes, so they can be used to guess passwords.
Other Ways Hackers Can Obtain Your Password
Manually cracking passwords is not the only way that hackers can obtain a target’s password. For example, phishing attacks are often used to obtain passwords.
In password-focused phishing attacks, a hacker will masquerade as a legitimate company and ask victims to input their password into a fake version of that company’s site.
Rather than spending time cracking the password, the hacker coaxes the user to hand over the password themselves using an email like the one below (Image Credit: FTC):
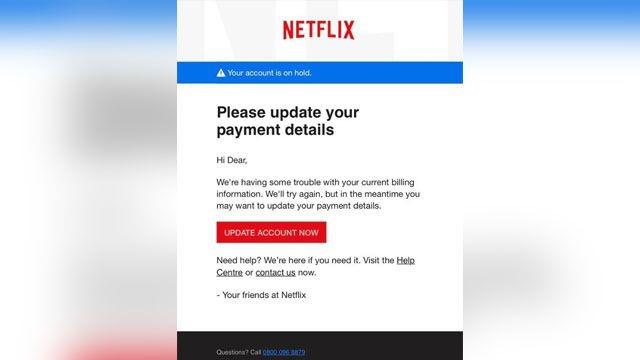
Password security is not just about making your password sufficiently long and complex – it’s also about being cautious about where you input your details.
Man-in-the-middle attacks – within which a threat actor positions themselves between two systems, one or both of which are compromised in some way – have also proven an effective tactic for cybercriminals looking to steal credentials.
Another way for a hacker to obtain your password is via a data breach. Rather than targeting individuals, hackers will target companies, hoping to find network vulnerabilities and extract password/hash data from their stored data.
Aside from ensuring you only hand over your personal data to companies with good security infrastructure and clean track records, there’s very little you can do to stop a data breach. If you stay up-to-date with news around the topic, however, you’ll be able to respond quickly and change your passwords if you’re affected. Some password managers will even alert you when there is a breach that affects your information, and can contribute to good data hygiene practices.
How to Improve Password Security
If your present passwords are relatively weak, don’t panic – there are a number of different ways you can improve your password security beyond using a tool to test your password strength.
Length, complexity, and uniqueness
There are three golden rules to improving the strength of your password: length, character variety, and uniqueness. All passwords should be at least 12 characters long, but this is really a minimum requirement. Making them even longer than this is strongly advised.
As you can see from the table included at the start of this article, having numbers, lower case letters, upper case letters, and symbols (sometimes called “special characters”) will make your password significantly more secure.
Activate multi-factor authentication
Multi-factor authentication (MFA) – one version of which is the common “two-factor authentication” (2FA) option provided by a lot of websites – is an easy way to significantly improve your password security.
When activated, MFA/2FA adds at least one more layer of security beyond your password. MFA systems typically require users to enter codes sent to their devices upon entry of correct passwords.
With MFA activated, a hacker could guess your password correctly, but would still be unable to access your account because they wouldn’t have the code sent to your device.
If you can, we’d advise opting for an authenticator app, such as Google Authenticator, over your phone number. Although uncommon, there are some techniques – such as SIM-swapping – that can be used to “hack” two-factor authentication via phone numbers.
Remember, activating multi-factor authentication isn’t a silver bullet – and it’s certainly not a substitute for a strong password. When activated on programs like Gmail, Google will also give you location and device information so you can be sure a login in attempt isn’t suspicious:

Use a password manager
The easiest way to ensure all of your passwords meet the above conditions is to use a password manager. Very few people will be able to remember sufficiently long, varied, and unique passwords for the array of accounts they currently use, so having a secure place to store them helps massively.
The best password managers deploy a zero-trust security architecture that makes it near-impossible to obtain passwords stored in their vaults, even if a hacker breaches their systems.
However, not all password managers are as reliable as each other, so we’d recommend opting for a provider that has a clean security record, excellent security infrastructure, and a robust privacy policy that explains exactly how it’ll keep your data secure.
Passwords vs Passphrases
In recent years, against a backdrop of cyber-attacks and data breaches, some cybersecurity experts have suggested that instead of using a password, you should use a passphrase, as this is a more secure way to protect an account.
Although password complexity is important – and a complex password will be more secure than a simple one – length is more important. So, a phrase made up of multiple words – which may also be easier to remember – is a better option in theory.
According to Hive, a 7-character password that uses the wides range of characters can be cracked in just four seconds – but an 18-character password of exclusively lowercase letters takes 481,000 years to crack.
As passphrases are not as common as passwords, hackers will not necessarily attempt to crack passphrases with the same rigor or intensity as they will passwords. Also, the use of spaces – which many people do not use in their passwords – adds another layer of variability.
It’s an interesting concept and something to consider when you create a new password. However, it must be stressed that creating a long passphrase that also incorporates a variety of different characters is the most secure option.
Final Thoughts: Securing Your Accounts Today
Unfortunately, it’s now pretty easy for hackers to guess uncomplicated passwords, particularly ones that aren’t very long. In fact, if your password is under 10 characters, it’ll only take 2 weeks to crack. Simple 10-character passwords made up of just numbers or lowercase letters can be cracked in under 24 hours.
Considering the prevalence of cyberattacks and the ease at which simple passwords can be guessed, it’s never been more important to use the tools available to you to secure your accounts. We recommend using a password manager to ensure you can use complex, lengthy, and unique passwords for all your accounts without having to remember them. This will make it significantly harder for hackers to crack your password.
Remember, there are other ways that hackers can obtain your password too, such as phishing attacks – so you must stay vigilant when leafing through your emails, text messages, and other digital correspondence, as well as when you set your account security credentials.


