A new phishing campaign has found a unique solution to hiding malicious URLs: Turn them into Morse code.
That’s right, the 1800s’ most popular form of telecommunication is making a comeback, and it wants your security information.
How it works
Phishing relies on tricking readers into opening up a seemingly legit email, clicking a link, and entering their personal details to be harvested. The problem is email readers everywhere are increasingly savvy to the scam, if the email even makes it through the spam filter at all.
One particularly targeted phishing campaign is rising to the challenge, according to a new report out from info-sec publication BleepingComputer.
The attack starts with an emailed HTML attachment that looks like an Excel invoice for the company it’s addressed to. This attachment uses JavaScript to map letters and numbers to Morse code, the communication system that uses a series of dots and dashes to represent each letter in the alphabet.
“The script then calls a decodeMorse() function to decode a Morse code string into a hexadecimal string. This hexadecimal string is further decoded into JavaScript tags that are injected into the HTML page. These injected scripts combined with the HTML attachment contain the various resources necessary to render a fake Excel spreadsheet that states their sign-in timed out and prompts them to enter their password again.”
Once a password is entered, the phishing attack has been successful.
While the level of sophistication at work here is debatable, there’s no arguing that it’s a novel approach.

The Morse code itself, via BleepingComputer
Who’s getting targeted?
There was some discussion of the validity of the entire attack on a Reddit post over at r/sysadmin, where the process was first discovered. But according to BleepingComputer, the attack has been found to be aimed at eleven different companies:
“BleepingComputer has seen eleven companies targeted by this phishing attack, including SGS, Dimensional, Metrohm, SBI (Mauritius) Ltd, NUOVO IMAIE, Bridgestone, Cargeas, ODDO BHF Asset Management, Dea Capital, Equinti, and Capital Four.”
The email is modified so that the attachment file matches the company name, and it uses the logo.clearbit.com service to insert the correct company logo into the fake login form. If there’s no logo, the generic Office 365 logo is used instead.
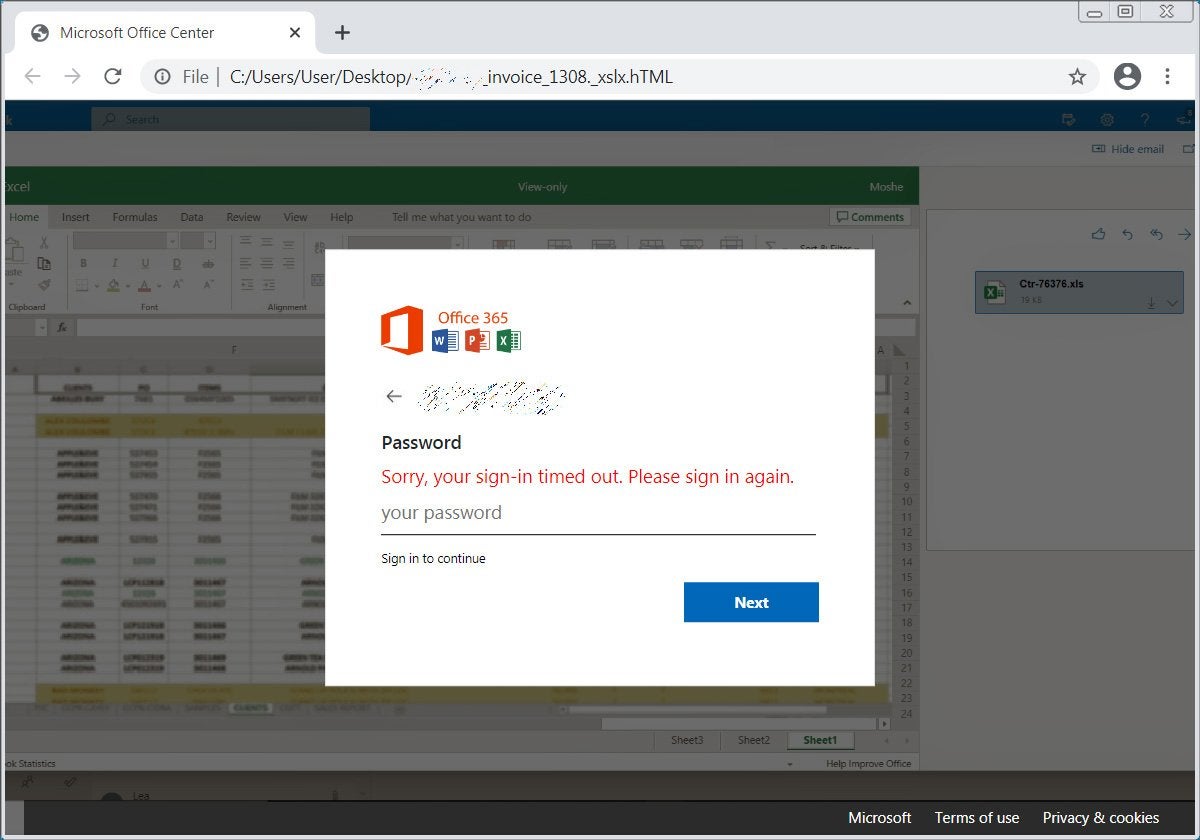
Fake Office 365 sign-in, via BleepingComputer
Staying safe
If you’re not one of those eleven companies, you’re likely safe from the world’s most old-timey phishing attempt, at least until they start trying smoke signals.
But while Morse code is unlikely to take off, plenty of other phishers are actually posing a danger to individuals as well as businesses. And it’s an arms race when it comes to online security, with email clients shoring up their spam filters on one hand while phishers come up with new phrases or code substitutions to slip past those filters on the other hand.
Ultimately, there’s no one perfect solution, though the right tips can help: Look at the URLs in the emails, check email addresses carefully, and employ two-factor authentication to ensure that even if your password leaks, the phishers won’t be able to use it. Finally, grabbing a good password manager for a few dollars a month can go far towards protecting you.




