Voice over Internet Protocol (VoIP) has quickly become the new norm for business telephone systems. It’s faster, clearer, and more efficient for companies of all sizes to conduct business over the phone, rather than landline systems. But is VoIP secure?
Like any platform that transmits data via the internet, VoIP systems can be targeted by bad actors – and with 82% of breaches involving data stored in the cloud (Source: IBM), businesses using VoIP need to be extra vigilant.
But your business telephone system needn’t be a source of stress. Understanding the importance of VoIP security and taking steps to get set up with a secure VoIP provider is the best way to ensure you’re safe. We’re here to walk you through the details.
In this guide:
How Secure Is VoIP?
Like almost all technology that connects to the internet in some way, VoIP systems can be compromised. Famously, cybercriminals gained illicit access to 3CX last year, using the platform to target unsuspecting customers.
How secure your VoIP system depends significantly on how secure your company’s IT and internet infrastructure is.
Last year, 83% of organizations experienced a data breach, so if you’re not bolstering your company’s defenses where you can, there’s every chance you could fall victim to one of these attacks.
Follow our best practices to greatly reduce your chances of getting compromised. However, it’s also important to pick a VoIP provider that implements best-in-class encryption measures, which we’ll dig into in more detail below.
Is VoIP More Secure Than Landline?
Landline phones aren’t connected to the internet and don’t rely on it in order to function, which leads some people to believe they’re a bit more secure than VoIP phones. Conventional wisdom suggests that it would be easier for a criminal to manipulate or store digital data being transferred during VoIP calls than the data transmitted between landline phones.
However, it’s entirely possible for a landline phone system to be accessed – a process referred to as “wiretapping.” This is one of the risks of having a confidential conversation over a publicly switched telephone network (PTSN). Landlines are by no means infallible.
Although it may be easier to eavesdrop on a VoIP call than wiretapping a landline, protecting VoIP phones is significantly easier, as well as cheaper, than protecting the average landline phone network. For example, you can encrypt VoIP calls on many platforms, including RingCentral and Zoom, usually for relatively little cost.
If you configure your VoIP system with the appropriate security measures, you can make it just as secure as a landline, if not more secure. If you’re considering the switch between the two types of phone systems, be sure to find out more about the differences between VoIP and Landline phones.
The Importance of VoIP Security
You might be wondering – how important is VoIP security really?
Simply put, the importance of VoIP security cannot be understated. On a more specific note, because VoIP technology relies on the internet to make calls, it’s inherently vulnerable to certain attacks. Given that more than 25% of Wi-Fi networks around the world are without any form on encryption, a VoIP provider that is lax on security could cause some serious problems for your business.
If you’re running a business in the US, the odds are much higher (34%-44%) that the network your using is unencrypted, which means you really need to make sure that you choose a trusted VoIP provider that follows best practices.
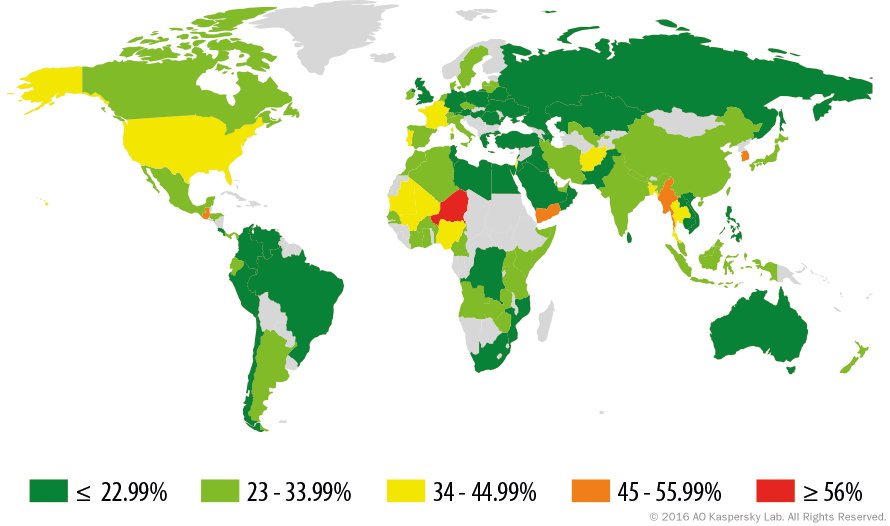
World map showing the percentage of unencrypted WiFi networks by country. Source: Kapersky Lab
VoIP Security Threats
Unfortunately, a VoIP vulnerability leaves you wide open to a whole array of challenges, from a simple nuisance to a full-blown security breach. The best way to ensure your VoIP system stays secure is to know what might be out there. Here are a few of the most notable VoIP security threats and consequences:
Malware
As with any system that is connected to the internet, VoIP systems are susceptible to malware attacks, as well as other viruses that could slow down or compromise your system.
VoIP phishing
Also known as Vishing, this attack is designed to target specific phone users, duping them into believing that the call is from a reputable source through Caller ID and convincing them to provide valuable personal and company information that could lead to a security breach.
VoIP Breaching Tools
Specific tools, like Voice Over Misconfigured Internet Protocol (VOMIT), can be used to prey on unencrypted IP phone calls.
Denial of Service (DoS)
This attack is specifically made to disrupt phone service. It overloads the system, depriving it of important resources, which eventually leads to poor call quality, uptime, and latency.
Eavesdropping
If your VoIP system is set up on an unencrypted WiFi network, you could have nefarious actors listening in on conversations with ease. This could lead to a serious security breach, particularly if you are discussing sensitive information.
Robocalls
More of an annoyance than a serious threat, but voicemail functionality opens the door to pretty much anyone to leave a message, including robocalls and other spammers.
The Threat of AI
New security threats are emerging all the time and, with the increasing sophistication of AI models, becoming harder to detect. A July 2023 study showed that AI tools can identify the specific keys that users type on VoIP calls with over 95% accuracy. That means that if a cyber criminal is able to break into a call and eavesdrop on it, they may be able to extract sensitive information that isn’t even discussed aloud.
What’s more, AI can be used to carry out malicious voice scams, in which a specific person’s likeness is used to deceive unsuspecting victims. In January this year, New Hampshire citizens were sent phone messages from a source claiming to be Joe Biden in which they were encouraged to not vote in their state primary. In reality, the voice was generated by AI.
With AI development accelerating at a dizzying rate, the landscape of cybercrime will look a lot different in 12 months. It’s vital to stay vigilant and read up on the latest threats. And to make sure your business is protected today, check out our 12 essential cybersecurity measures.
Use a strong password and multi-factor authentication
You need to pick a strong, memorable password that won’t be easily guessed. Password best practices dictate that it should be at least 10 characters long. Alongside this, you should consider additional measures, like password expiration dates or multi-factor authentication (MFA). They will greatly enhance your system security.
Some VoIP providers, like Vonage, now offer comprehensive protection suites that will let you implement MFA across multiple channels, and include a collection of other useful fraud prevention tools.
Add your VoIP system to your firewall
Like other devices and systems contained within your company’s IT infrastructure, your VoIP system should be shielded behind your corporate firewall. Although VoIP systems have a lot of security features, they won’t cover everything, and you’ll have to take some responsibility for securing it within your existing perimeter.
If you add your VoIP system to your firewall, you’ll be able to monitor for – and block – suspicious and unauthorized activity on your network.
Update your system regularly
It may seem like a hassle, but when it comes to online security, updating your software on a consistent basis can go a long way to protecting your devices. This is especially true for VoIP phone systems, as providers regularly experience attempted breaches that can only be closed with swift and effective software updates.
Monitor your call logs
Another surefire way to make sure your VoIP system is secure is to actually keep an eye on it. Most VoIP providers will allow you to take a look at call logs, giving you a clear breakdown of who is calling where and how often, allowing you to monitor for any suspicious behavior that could lead to a security breach. Be on the lookout for strange numbers, odd hours, and anything that seems out of the ordinary.
Require remote employees to use a VPN
Employees working from home can open up a whole array of security vulnerabilities, particularly if you have them logging into the company phone system from a smartphone or connected phone system at their home.
To avoid any security pitfalls, make sure your team is required to use a VPN for all at-home usage. This will protect their internet activity from external sources, including phone calls on a VoIP system, so there is no risk of an unsecured WiFi network creating problems for your business.
Check out our in-depth business VPN guide for more info
Educate your team
As a business owner or security manager, understanding all these VoIP security best practices is obviously important, but not nearly as important as relaying them to your team. In fact, all the knowledge in the world won’t help you unless you pass it on, which is why educating your team about security best practices, for VoIP or otherwise, is an integral aspect of running a successful, breach-free company.
How to Choose a Secure VoIP Provider
Now that you understand how important VoIP security is and how to follow best practices, you need to know which providers are actually looking out for your protection. Fortunately, there are three key elements that can help you know for sure whether or not you’ve found a secure VoIP provider: encryption, support, and compliance accreditation.
Encryption
To avoid getting too complicated, encryption is essentially the process of making internet data more secure. In the same way an unencrypted Wi-Fi network can compromise your security, providers that don’t offer call encryption will leave you open to a wide range of potential breaches.
You want to make sure your VoIP provider is offering Transport Layer Security (TLS) and Secure Real-time Transport Protocol (SRTP), the two most common and necessary protocols for VoIP technology.
Not all VoIP providers offer the same levels of encryption. For example, RingCentral, one of the most popular and feature-rich business telephone systems currently available, only added end-to-end encryption for its phone and messaging communications at the end of last year.
Support
You’re going to want help from the experts when you need it, so reading up on what different vendors offer is essential. From sporadic hours and live chat to 24/7 phone support, different providers have varying levels of support available. Make sure you choose the one that’s right for your business.
Compliance accreditation
Because concerns about data security are so prevalent in the world today, there are plenty of regulations out there designed to keep people safe. Unfortunately, not all providers follow these regulations, shirking their responsibility to be compliant with specific measures. Be sure to check which accreditations your provider has before signing off.
Getting Started with a Secure VoIP Phone System
Now, if all this talk about security breaches hasn’t scared you off, getting started with a VoIP phone system shouldn’t be too hard at all. Tech.co has done extensive research to identify the best VoIP phone providers, and you can compare prices for your business with just the click of a button. Simply take advantage of our handy comparison tool, to receive tailored, accurate pricing for your business, without breaking a sweat.
The most secure VoIP solution we’ve found is Google Voice. While all the top VoIP providers use multiple security methods, Google Voices hits it out of the park when it comes to these, adding every known protection and scoring 5/5, a higher score than competitors such as Vonage, 8×8 and RingCentral.
If you click on, sign up to a service through, or make a purchase through the links on our site, or use our quotes tool to receive custom pricing for your business needs, we may earn a referral fee from the supplier(s) of the technology you’re interested in. This helps Tech.co to provide free information and reviews, and carries no additional cost to you. Most importantly, it doesn’t affect our editorial impartiality. Ratings and rankings on Tech.co cannot be bought. Our reviews are based on objective research analysis. Rare exceptions to this will be marked clearly as a ‘sponsored’ table column, or explained by a full advertising disclosure on the page, in place of this one. Click to return to top of page
